openswan IPSec |
您所在的位置:网站首页 › ipsec openwrt › openswan IPSec |
openswan IPSec
|
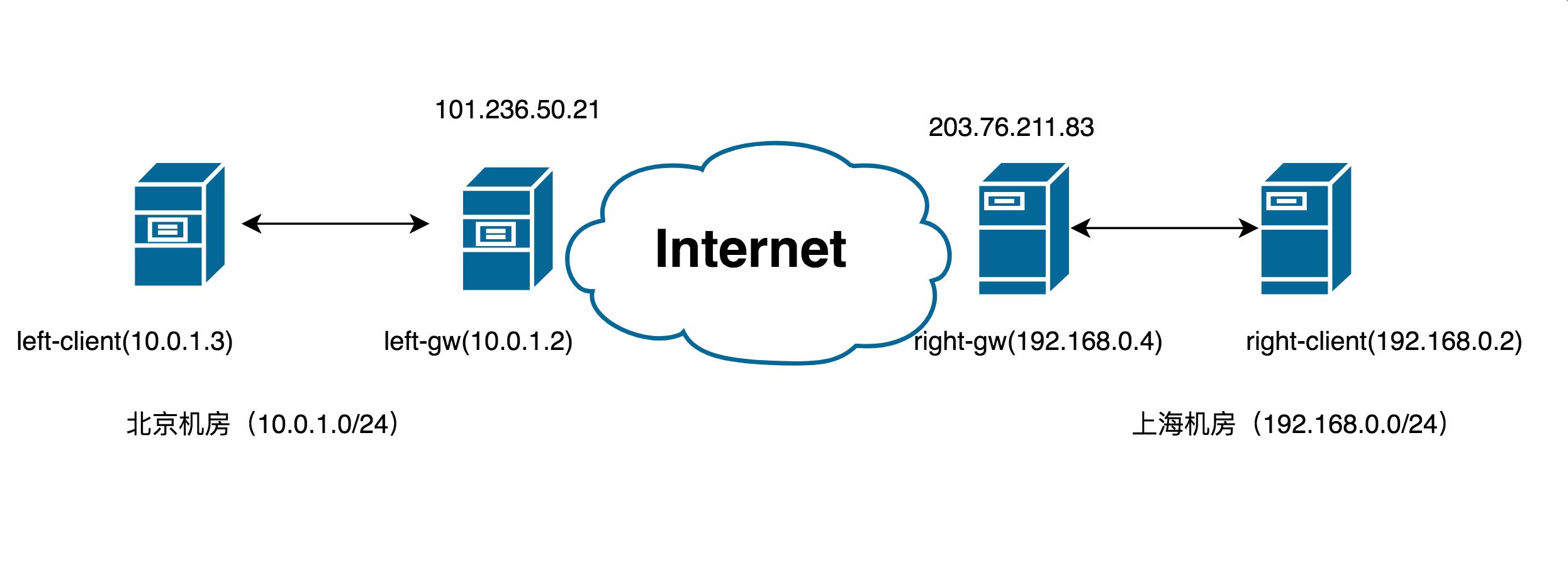
简介 本文介绍IPSecVPN的搭建过程,并通过公网将分属于美团云上海与北京两个机房内的vpc子网打通。由于美团云经典网络在网络控制器上对ip_filter 做了限制,打通前需要确保两边网络都处于VPC下,且子网网段无交集。当前部署环境为CentOS 6.5。 一、网络模型计划实现的效果是,从左侧vpc网络上的left-client主机,可以ping通右侧vpc中right-client主机内网IP
此处环境配置,主要是针对两台用做gw的主机:left-gw和right-gw 1 内核参数 # vim /etc/sysctl.conf net.ipv4.ip_forward = 1 net.ipv4.conf.default.rp_filter = 0 net.ipv4.conf.eth0.rp_filter = 0 net.ipv4.conf.eth1.rp_filter = 0 关闭icmp重定向 # sysctl -a | egrep "ipv4.*(accept|send)_redirects" | awk -F "=" '{print$1"= 0"}' >> /etc/sysctl.conf # sysctl -p 2 OpenSwan配置通过yum安装OpenSwan (ipsec) sudo yum -y install openswan安装完毕后,可以看到实际安装的版本为Libreswan3.15 , 是因为最原始的OpenSwan已不再更新。 # ipsec --version Linux Libreswan 3.15 (netkey) on 2.6.32-696.1.1.el6.x86_64执行下ipsec verify,确认配置正常: # ipsec verify Verifying installed system and configuration files Version check and ipsec on-path [OK] Libreswan 3.15 (netkey) on 2.6.32-431.1.2.0.1.el6.x86_64 Checking for IPsec support in kernel [OK] NETKEY: Testing XFRM related proc values ICMP default/send_redirects [OK] ICMP default/accept_redirects [OK] XFRM larval drop [OK] Pluto ipsec.conf syntax [OK] Hardware random device [N/A] Two or more interfaces found, checking IP forwarding [OK] Checking rp_filter [OK] Checking that pluto is running [OK] Pluto listening for IKE on udp 500 [OK] Pluto listening for IKE/NAT-T on udp 4500 [OK] Pluto ipsec.secret syntax [OK] Checking 'ip' command [OK] Checking 'iptables' command [OK] Checking 'prelink' command does not interfere with FIPSChecking for obsolete ipsec.conf options [OK] Opportunistic Encryption [DISABLED]vim /etc/ipsec.conf 编辑配置文件 version 2 # basic configuration config setup # which IPsec stack to use, "netkey" (the default), "klips" or "mast". # For MacOSX use "bsd" protostack=netkey //使用2.6内核内建模块netkey,2.6以下是KLIPS模块 nat_traversal=yes virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10 dumpdir=/var/run/pluto/ logfile=/var/log/pluto.log //log location conn net-to-net authby=secret //使用预共享密钥方式进行认证 type=tunnel left=101.236.50.21 leftsubnet=10.0.1.0/24 leftid=@test1 //一端的标识符,可以任意填写,如果多个连接需要区分 leftnexthop=%defaultroute right=203.76.211.83 rightsubnet=192.168.0.0/24 rightid=@test2 rightnexthop=%defaultroute ike=aes256-sha2_256;modp2048 phase2alg=aes256-sha2_256;modp2048 auto=add //add代表只是添加,但并不会连接,如果为start则代表着启动自动连接两台主机是完全相同的配置,可以直接将ipsec.conf的配置文件scp 到另一台gw server上 我们使用基于pre-shared keys认证方式(PSK), 在101.236.50.21上: vim /etc/ipsec.secrets 101.236.50.21 %any 0.0.0.0 : PSK "123"这个文件的格式为:“Local Ip address” “remote ip address” : PSK “your key” 若本身不存在/etc/ipsec.secrets ,可以执行下述命令先生成此文件: ipsec newhostkey --output /etc/ipsec.secrets同理在右侧right-gw机器上也做相应配置。 重启两个vpn服务: service ipsec restart在其中一台主机上启动connect: # ipsec auto --up net-to-net 002 "net-to-net" #1: initiating Main Mode 104 "net-to-net" #1: STATE_MAIN_I1: initiate 003 "net-to-net" #1: received Vendor ID payload [Dead Peer Detection] 003 "net-to-net" #1: received Vendor ID payload [FRAGMENTATION] 003 "net-to-net" #1: received Vendor ID payload [RFC 3947] 002 "net-to-net" #1: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal) 002 "net-to-net" #1: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2 106 "net-to-net" #1: STATE_MAIN_I2: sent MI2, expecting MR2 003 "net-to-net" #1: NAT-Traversal: Result using RFC 3947 (NAT-Traversal) sender port 500: no NAT detected 002 "net-to-net" #1: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3 108 "net-to-net" #1: STATE_MAIN_I3: sent MI3, expecting MR3 003 "net-to-net" #1: received Vendor ID payload [CAN-IKEv2] 002 "net-to-net" #1: Main mode peer ID is ID_FQDN: '@test2' 002 "net-to-net" #1: transition from state STATE_MAIN_I3 to state STATE_MAIN_I4 004 "net-to-net" #1: STATE_MAIN_I4: ISAKMP SA established {auth=PRESHARED_KEY cipher=aes_256 integ=sha group=MODP2048} 002 "net-to-net" #2: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP+IKEV1_ALLOW+IKEV2_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW {using isakmp#1 msgid:f72303da proposal=defaults pfsgroup=OAKLEY_GROUP_MODP2048} 117 "net-to-net" #2: STATE_QUICK_I1: initiate 002 "net-to-net" #2: transition from state STATE_QUICK_I1 to state STATE_QUICK_I2 004 "net-to-net" #2: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP=>0x5e6e7359 |
【本文地址】